Encrypted Disk¶
The option to request disk encryption adds layers of complexity in server administration as every time the system is rebooted The drive needs to be decrypted and this can only be done by accessing viaSSH.
If you have chosen this option you will not be able to access the full control panel features until you have changed the passwords to unlock the disk.
The same control panel detects if you have already done this step. If not it will redirect you to the corresponding page.
The control panel allows you to assign 2 passwords for the first two slots (Slot 0 and Slot 1) even though LUKS2 allows many more: https://unix.stackexchange.com/questions/553691/how-many-key-slots-does-the-luks2-support. You can add more Slots from the console if you wish.
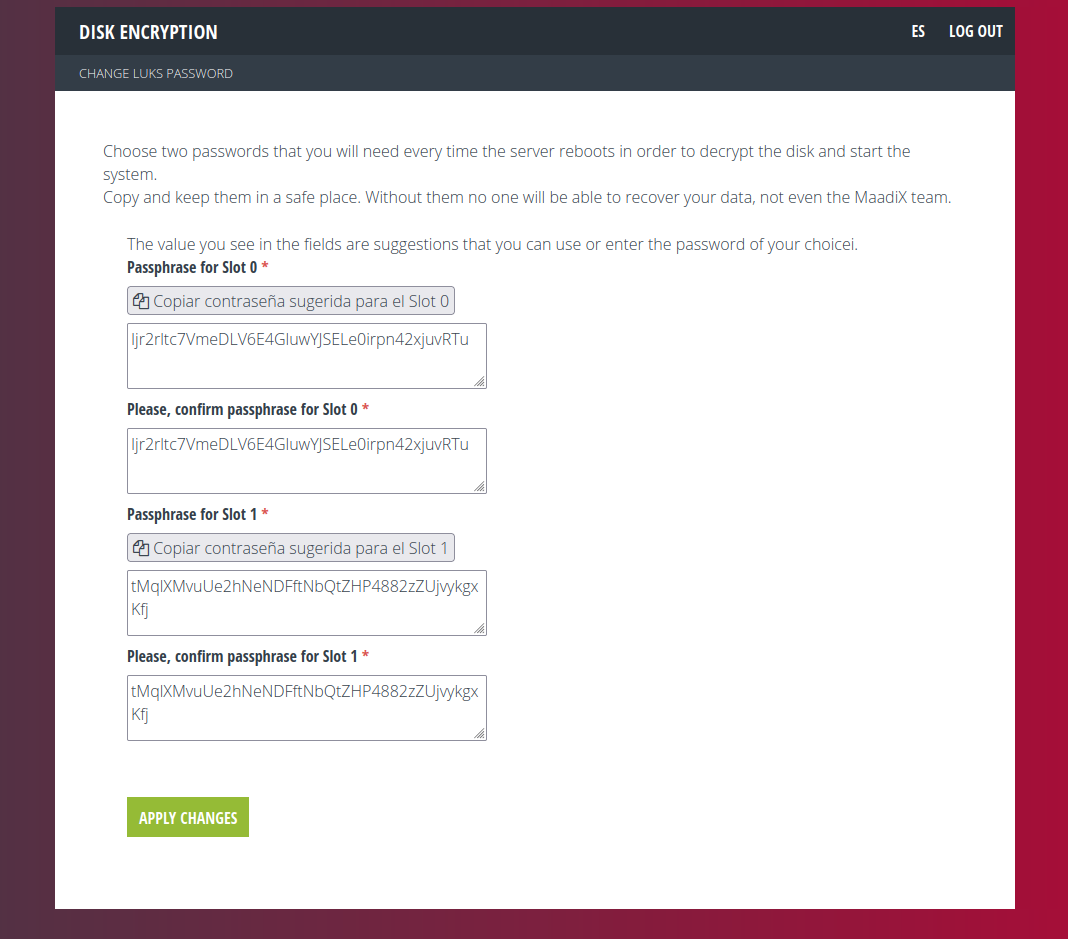
You will have to choose two new passwords which will have to be at least 32 characters and may not include special characters such as {[*$^ etc.
This limitation is due to the fact that it may happen that the language of your keyboard does not match the one on the console for the disk unlocking which would cause a mismatch between the password you insert and the one the system actually receives.
For this reason, the form provides a suggested password for each Slot as well as a button to copy the whole string, in order to avoid errors.
You will have to confirm the password for each Slot and above all copy and save each one in a safe place. Remember that if you lose these passwords you will not be able to access the system once it restarts and the MaadiX team will have no way to fix it.
As a last step you will have to enter the password you use to access the control panel.
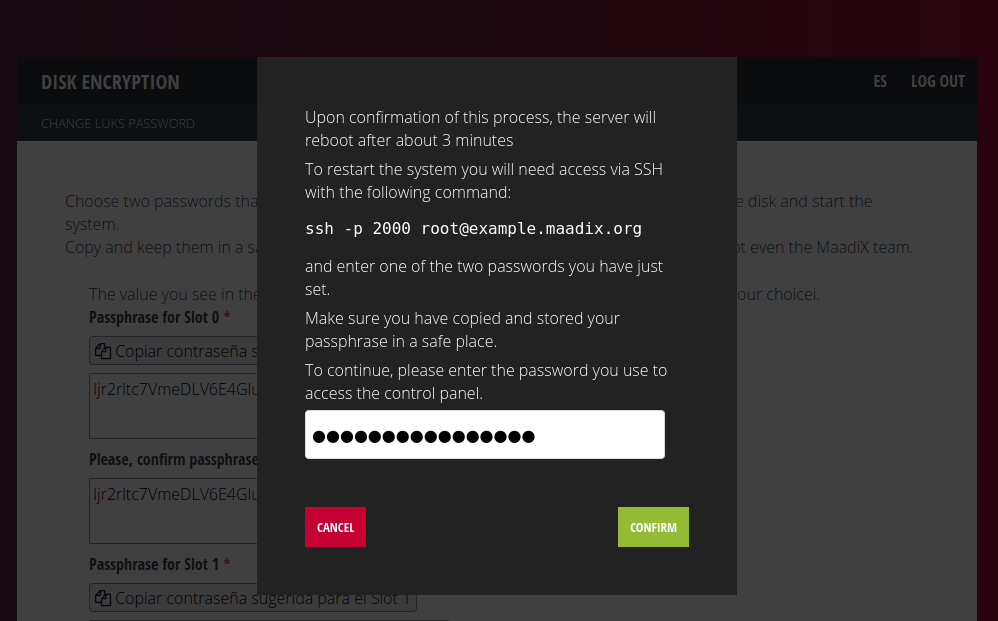
Once you click the ‘Confirm’ button, the system will set up the two new passwords you have just chosen and when it is finished (after about three minutes) it will automatically reboot the server.
This will allow you to check if you can decrypt the disk and boot the system before inserting any data. To do this, you will need to access via SSH to the server on port 2000 with the command:
ssh -p 2000 root@myserver.maadix.orgby replacing myserver.maadix.org with the name of your server, or:
ssh -p 2000 root@XX.XX.XX.XXreplacing XX.XX.XX.XX.XX with the IP of your server
If the server has already rebooted you will see a console with this message:
Please unlock disk cryptroot:
Insert one of the two passwords and press the ENTER key.
If the following messages appear on the console:
cryptsetup: cryptroot set up successfully Connection to mysqerver.maadix.org closed.
It means that the disk has been decrypted and the system is booting. Your connection to port 2000 has been closed and to get back to to log in via ssh, you will have to use the configured port (by default is 22).
At this point you can reboot the server to check the second password.
Backup¶
If the header of a LUKS volume is damaged, all data is permanently lost unless there is a backup copy of the header. If a key slot is damaged, it can only be restored from a backup of the header or if there is another undamaged Slot with a known passphrase. LUKS header damage is something that can happen with surprising frequency.
There are two critical components to decryption: The header itself and theSlots. If the header is damaged and a backup copy is not available, nothing can be done to access the data. If a Slot is damaged, the data can be accessed if there is another undamaged Slot.
This is why it is very important to have more than one Slot and to make a backup copy of the header.
In Servers provided by MaadiX the LUKS volume is /dev/vda2 and you can make a copy of the header with the following command:
sudo cryptsetup luksHeaderBackup /dev/sda2 --header-backup-file /root/sda2-header-backup
You will need to copy the /root/sda2-header-backup file to an external device.
More details can be found in this tutorial: https://www.lisenet.com/2013/luks-add-keys-backup-and-restore-volume-header/