Unban Access
Servers with MaadiX have two methods to minimize unauthorized authentication attempts: Fail2ban and Tally2.
Fail2ban
Fail2ban is a software that is used to prevent massive connection attempts, it is free software and in MaadiX it comes installed by default. The basic function of Fail2ban is to prevent intrusions that may come from brute force attacks (attacks that consist of testing thousands of connection attempts to try to find a valid user/password combination).
It works as follows: when there are a certain number of unsuccessful attempts to access the server, fail2ban blocks the IP address from which access is attempted.
In Maadix, fail2ban is activated for the following services:
apache: the web server for web applications, nextcloud, discourse, etc
sshd: the protocol for remote and secure communication with our server to access the command line thorugh SSH or SFTP.
ssh-ddos: specific implementation of ssh to protect the server from distributed denial of service attacks (ddos).
dovecot: IMAP/POP3 server to connect to the email accounts.
mxcp: the MaadiX graphical interface (The Control Panel).
sasl: security framework installed on the server to synchronize and authenticate connection and authentication protocols.
Unlocking access
It may happen that a person repeatedly fails to insert the password trying to access a service and fail2ban blocks them. The duration of the blocking is 12h, except for the control panel which will only be 1h.
If a single person in an office makes a mistake or has a misconfigured mail client (Outlook/thunderbird, which periodically tries to authenticate to the mail server), this can impact all other people in the same office, since they use the same public Ip.
When this happens (and you don’t want to wait 12h to regain access) You can manually uniban the IP both from the control panel, as well as from the console, in order to re-grant access to legitimate accounts that may have been blocked due to errors and not unauthorised authentication attempts.
From the control panel:
In order to unlock access from the control panel you need to be able to login to it. If your own IP has been blocked you will have to access from a different one (Another office, VPN, Tor, Phone connection…)
Go to the System -> Unblock Access section of the control panel.
To unblock your IP you have first to figure out what is the public IP you are connecting from. You can search for ‘what is my ip’ with the search engine to find a website that will provide you with this information, for example https://cualesmiip.com.
It will return a result like this, where 123.45.67.32 would be your IP. Obviously if the person experiencing the block is located at another address/office, they will have to provide you with their own public IP, by visiting the link themselves.

You will have to insert this value in the ‘Unban IP’ field of the form that you find in the System -> Unban Accesses section of the control panel.
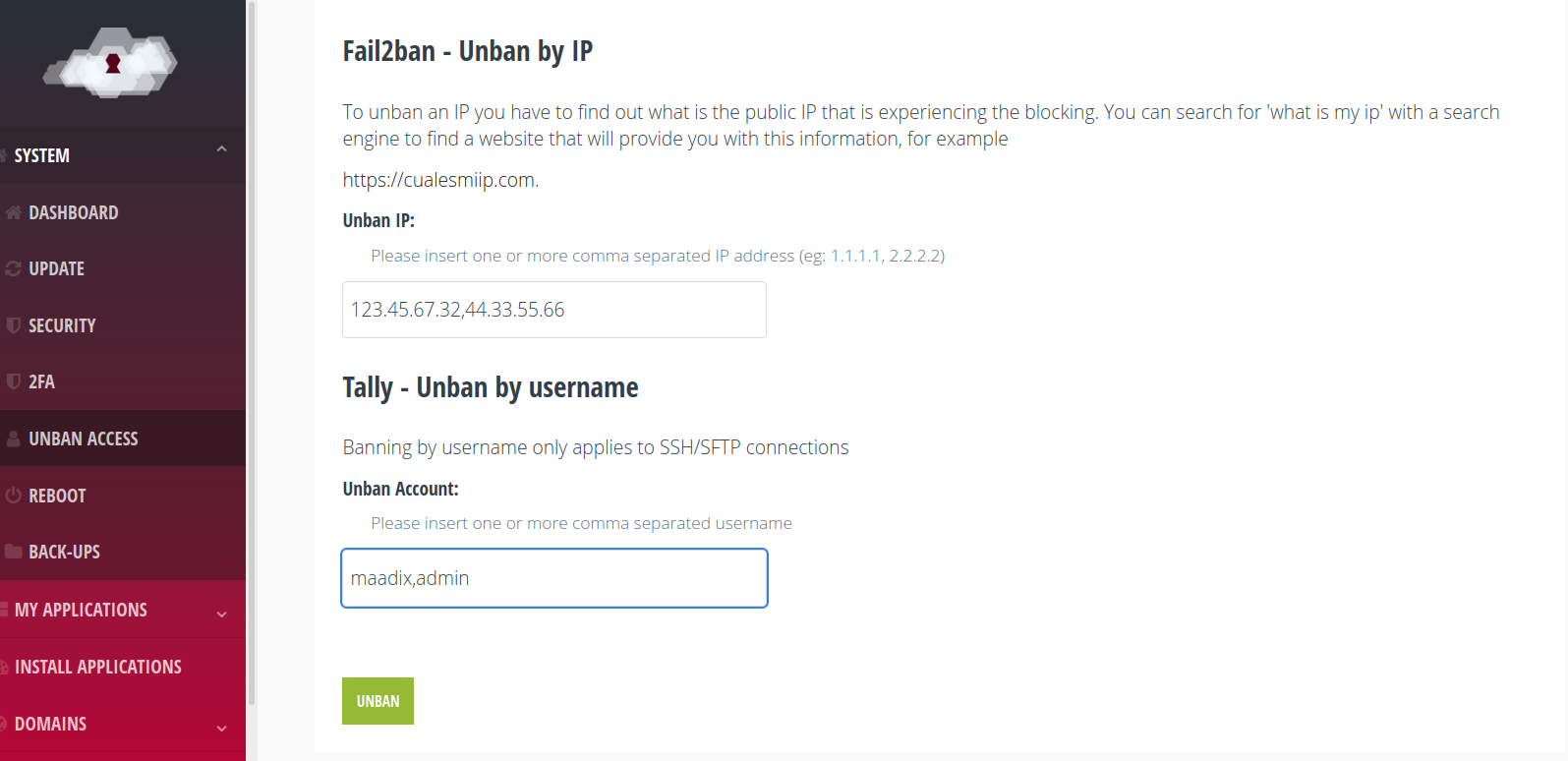
You can unlock more than one IP in the same action by inserting multiple comma-separated values.
SSH connections also have an extra layer of protection provided.by Tally2. This type of blocking uses the user name rather than the IP. That is, if the server had received too many failed SSH/SFTP authentication attempts with the ‘admin’ account, any subsequent authentication attempt for ‘admin’ would be blocked for 12 hours.
To recover access you can insert one or more username separated by comma in the ‘Unban Account’ field. So in this case you can insert the name of any SSH/SFTP account that you have created and that is experiencing access problems.
Once the form is submitted, the unban may take about three minutes, iso wait before trying to log in again.
From the console
You can also SSH into the server to unban the IP that has been blocked.
You will need to run commands for which system administration permissions are required, so you will need to login with the Superuser account:
ssh superuser@servername.maadix.net
Note: If it is your own IP that is blocked you will not be able to access the server, it will return a “Connection Refused” error. We recommend you connecting to a VPN, a different network, or using a cell phone data connection, so that you can log in from an IP other than the one that is blocked.
if you use the VPN connection of the same MaadiX server you want to access, the way to bypass the blocking is to access using the IP of the OpenVpn server with the following command: ssh username@10.8.0.1
To unblock an IP we must first find out which IP. You can go to any search engine to check “what is my ip”, hundreds of results will show the IP address of your connection (for example https://cualesmiip.com).
Remind that all the people of the same office or home, who are connected to the same router will go out to the Internet with the same IP (public IP), so it can happen that a whole office or home is denied access to the server (or any of its services).
At fail2ban, the protection for each of these services is called jails.
Once we know the blocked IP, it can be unblocked with the following command:
sudo fail2ban-client set <JAIL> unbanip <IP_TO_UNBLOCK>
Here you have some examples to unblock IP 4.4.4.4:
For SSH and SFTP connections:
sudo fail2ban-client set sshd unbanip 4.4.4.4
For Nextcloud, Owncloud, Rainloop (webmail) or other application that works over Apache:
sudo fail2ban-client set apache unbanip 4.4.4.4
For the control panel:
sudo fail2ban-client set mxcp unbanip 4.4.4.4
For imap and pop3 (access to emails)
sudo fail2ban-client set dovecot unbanip 4.4.4.4
For smtp (send e-mails):
sudo fail2ban-client set sasl unbanip 4.4.4.4
The jails enabled by default in MaadiX are: sshd, ssh-ddos, apache, dovecot, mxcp and sasl.
To check the status of each jail and see which IPs are blocked, you can run this command:
sudo fail2ban-client status <JAIL>
To check the status of each jail and see which IPs are blocked, you can this command:
sudo fail2ban-client status
You can check fail2ban logs at: /var/log/fail2ban.log
If you want to investigate more about fail2ban, you can visit the official Fail2ban website.
For Tally2, you can check the failed attempt counter for a given account with the following command:
# pam_tally2 --user=maadix
In the following case, we see that for the maadix account there are 5 failed attempts.
Login Failures Latest failure From maadix 5 01/01/21 21:22:37 172.11.11.51
It can be unlocked by resetting the counter as follows
# pam_tally2 --user=maadix --reset
If we launch the previous command again, the counter will return 0 and the maadix account will no longer be locked.