Security
In the control panel, in the ‘System’ tab, you will find the ‘Security’ section. Here you will be able to configure different options to reinforce the security of your server.
SSH
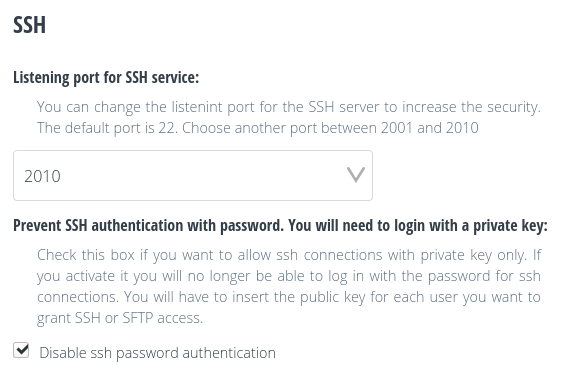
In the ‘SSH’ section you can configure the port for SSH connections. Choose from the drop-down list the port you want between 2001 and 2010 (by default, you will have port 22). Once changed, SSH connections will have to include the parameter with the new designated port, for example:
ssh -p 2001 user@myserver.maadix.org
Changing the SSH connection port strengthens your security because most attackers make connection attempts to port 22 (the default port for SSH).
In addition, you can check the ‘Disable SSH password authentication’ box so that connections to the server can only be made using SSH keys, not passwords.
This option will protect against any attempt to connect over SSH by unknown accounts trying to test different passwords.
After disabling SSH password access only the accounts to which you have added their public key (Usuarixs > Ordinary accounts > SSH key) will be able to connect to the server. This applies to both SSH and SFTP connections.
Remember that you can add an account’s public key both when creating or editing it. You can also add SSH key to the Superuser account. From MaadiX, we recommend it especially for this account.
If you do not disable password access, you will be able to access the server using both password and SSH key. This can be convenient so that users don’t have to type their password but it won’t add security to the system.
If you have doubts about how to generate and use SSH keys you can check this tutorial.
Security section for SSH.
TLS
TLS (Transport Layer Security) is a cryptographic protocol that provides secure communications on the Internet. There are different versions of this protocol (TLS 1.0, TLS 1.1, TLS 1.2) and it is currently recommended to use TLS 1.2. Previous versions are considered insecure as they contain security vulnerabilities, which have been corrected in TLS 1.2.
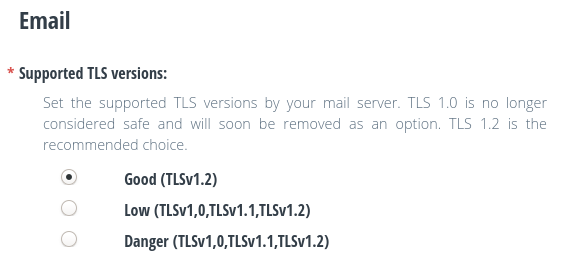
In the Email section you can configure which versions of TLS you want your mail server to support.
Security section on TLS versions (e-mail).
Although it is recommended to use only TLS 1.2, the option is given to also support older versions. This gives the possibility to receive or send mail to servers that use these versions (for example, older mail servers that don’t have TLS 1.2 enabled yet).
You can change the supported TLS versions whenever you want.
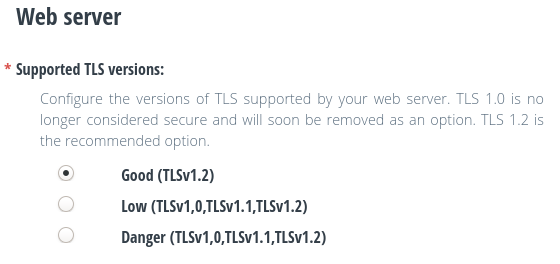
In the same way, in the Web Server section you will be able to establish which versions of TLS you want your web server to support. Likewise, only TLS 1.2 is the recommended option.
Security section on TLS versions (web server).
In this case, the web browsers will have to support TLS 1.2 in order to be able to consult the web pages hosted on your server. This will be the case in most browsers, only in the case of old browsers that only support older versions could cause problems.
You have the option of choosing between the supported versions to adapt to all needs. You will be able to change this configuration whenever you want.
Until you click on the ‘Save’ button, no changes will be made.
Rkhunter
Rkhunter is a tool for detecting rootkits, backdoors and other malware. It basically works by scanning important system files and comparing their hashes with an online database to ensure that they have not been modified. It also checks file permissions, looks for hidden files, dubious strings in kernel modules, rootkit default directories, etc
You can read more details on their official web site and view the code in its repository.
When Rkhunter detects any suspicious modifications to the system it sends an email alert listing the changes that Rkhunter has detected.
Rkhunter reports if a file has changed, but does not give information about what caused the change. For this reason false positives could be generated due to the installation or update of some package that Rkhunter registers as anomalous.
How to recognize legitimate changes?
Common false positives
False positives can occur both at the time of installation of new packages or applications, as well as in the upgrade process.
Application installations from the control panel
Some applications require the creation of an additional usuarix during the installation process. When a new account is added to the system, rkhunter sends an alert, regardless of the origin of this modification.
So after installing certain applications from the Control Panel, you may receive an email alerting you that new users and groups have been created in the system.
In the following table you have a list of users and groups that are created for each application. If after installing some of them you receive an alert as a new account has been created and there is a match with this table you can skip the alert.
Application |
User |
Group |
|---|---|---|
Etherpad |
etherpad |
etherpad |
Jitsi |
jicofo |
jitsi |
Jitsi |
jvb |
jitsi |
Jitsi |
prosody |
prosody |
Libre Office Online |
lool |
lool |
Mailman |
mailman |
mailman |
Mailtrain |
mailtrain |
mailtrain |
MongoDB (Rocketchat Dependency) |
mongodb |
mongodb |
Rocketchat |
rocketchat |
rocketchat |
coturn |
turnserver |
turnserver |
Spamassassin |
debian-spamd |
debian-spamd |
Here is an example of an email sent by Rkhunter after installing Jitsi, where you can see the alerts caused by the creation of different users and groups.
Example of mail:
Warning: User 'jvb' has been added to the passwd file.
Warning: User 'prosody' has been added to the passwd file.
Warning: User 'jicofo' has been added to the passwd file.
Warning: Changes found in the group file for group 'ssl-cert':
User 'prosody' has been added to the group
Warning: Group 'jitsi' has been added to the group file.
Warning: Group 'prosody' has been added to the group file.
The three accounts jvb, prosody and jicofo are necessary accounts for the installation of Jitsi, as you can see in the table above, so you can safely mute this alert from the control panel, so that Rkhunter will stop bothering you with this.
In the event of a mismatch, you should be sure of the source of the reported change before silencing the alert.
Updates
In MaadiX there is a system of automatic updates (Unattended Upgrades), which runs periodically and keeps the system up to date. It is possible that you will get an alert due to packages that have been automatically updated, such as ldd or syslogd. This is because for a period of time (in releases 202103-202201) the rkhunter configuration triggered alerts due to automatic updates.
If you upgrade MaadiX from the control panel you will apply a new system configuration in which changes generated by Unattended Upgrades will not trigger alerts from rkhunter.
However, if you run an update manually with the apt-get upgrade command, then you may receive the alerts. This is an example of an email you might receive in this case, where the curl package was updated:
Warning: The file properties have changed:
File: /usr/bin/curl
Current hash: 0e419fccc547bae9ff7fe2e7afa9cee381ce7305224f00a00bbd93fc087c600c
Stored hash : f180baed99bb09992aa231912c71254c637abb8993d2f52093c7711c06c9ae68
Current inode: 6689779 Stored inode: 6684934
Current file modification time: 1617137760 (30-mar-2021 22:56:00)
Stored file modification time : 1582383706 (22-feb-2020 16:01:46)
Manual Review
In addition to checking email alerts, you can also check the status of the system with the commands:
sudo rkhunter --check
sudo rkhunter --check --report-warnings-only (solo muestra las alertas)
These commands return the results of the checks that Rkhunter runs. In this screenshot we show an example of what the command returns from the terminal, on a system where no suspicious files have been detected:
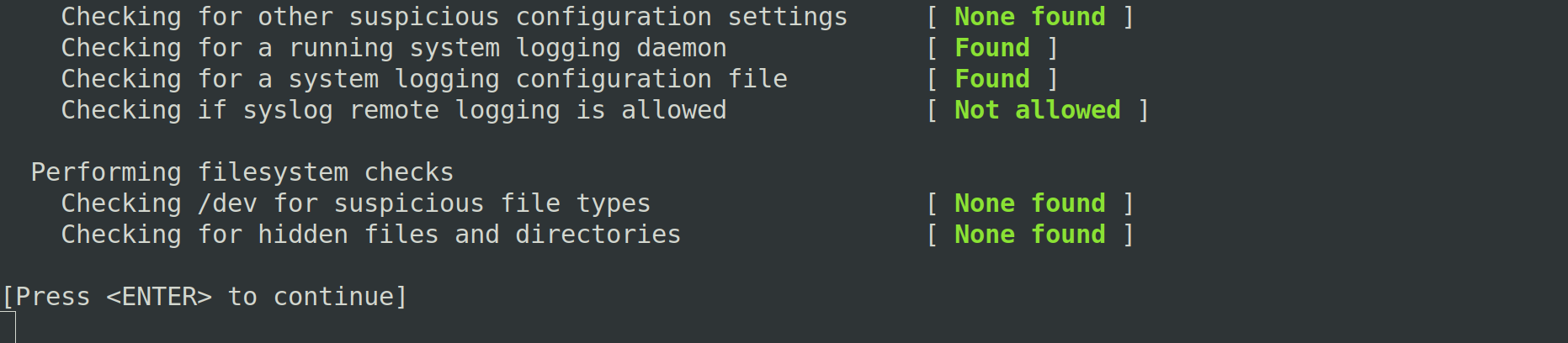
Example of Rkhunter check by terminal (status ok).
Now suppose that a suspicious file appears in the /etc directory. For the example we have created the hidden file .IamBad in the same directory. If we run the rkhunter --check command again, we can see how the result changes and we get the corresponding alert:
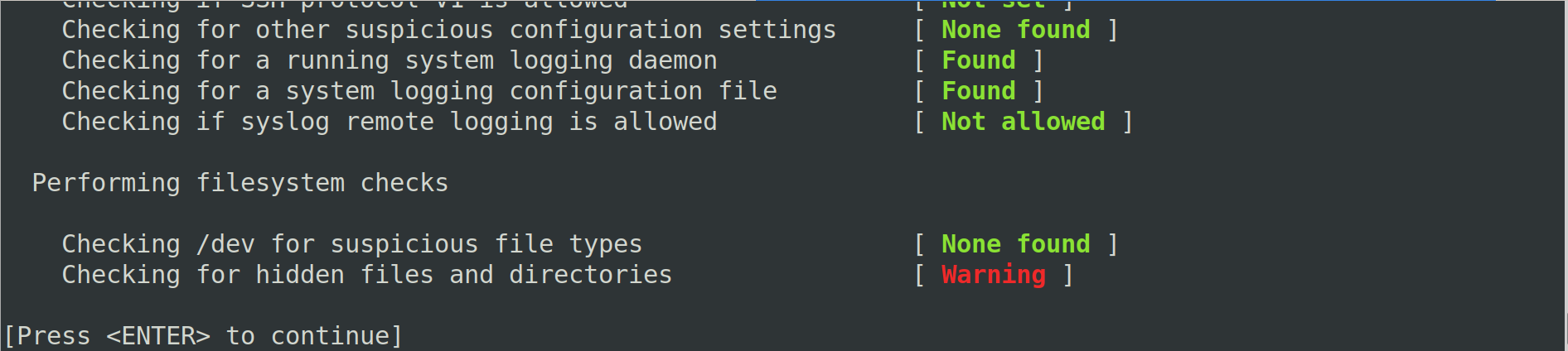
Example of Rkhunter check by terminal (hidden file suspicious).
So if you receive an email or when you run the above command you see an alert that you don’t recognise (e.g. that there are new hidden files in paths like /etc), then you should be concerned.
You can also check the logs in /var/log/rkhunter.log.
Muting Alerts
From the control panel you have the option to approve the alerts that Rkhunter has detected, so that it stops sending them by email. We would like to point out that before using this functionality, it is recommended that you check the alerts thoroughly to confirm that the changes that have been generated in the system correspond to any installation, configuration or update that you have previously carried out.
Once you have done this check, if Rkhunter is alerting you about a change that is legitimate (e.g. after performing an installation or configuration) you can go to the Control Panel, to the “Security” section, and click on the “Reset” button to stop receiving these alerts.
Reset Rkhunter.